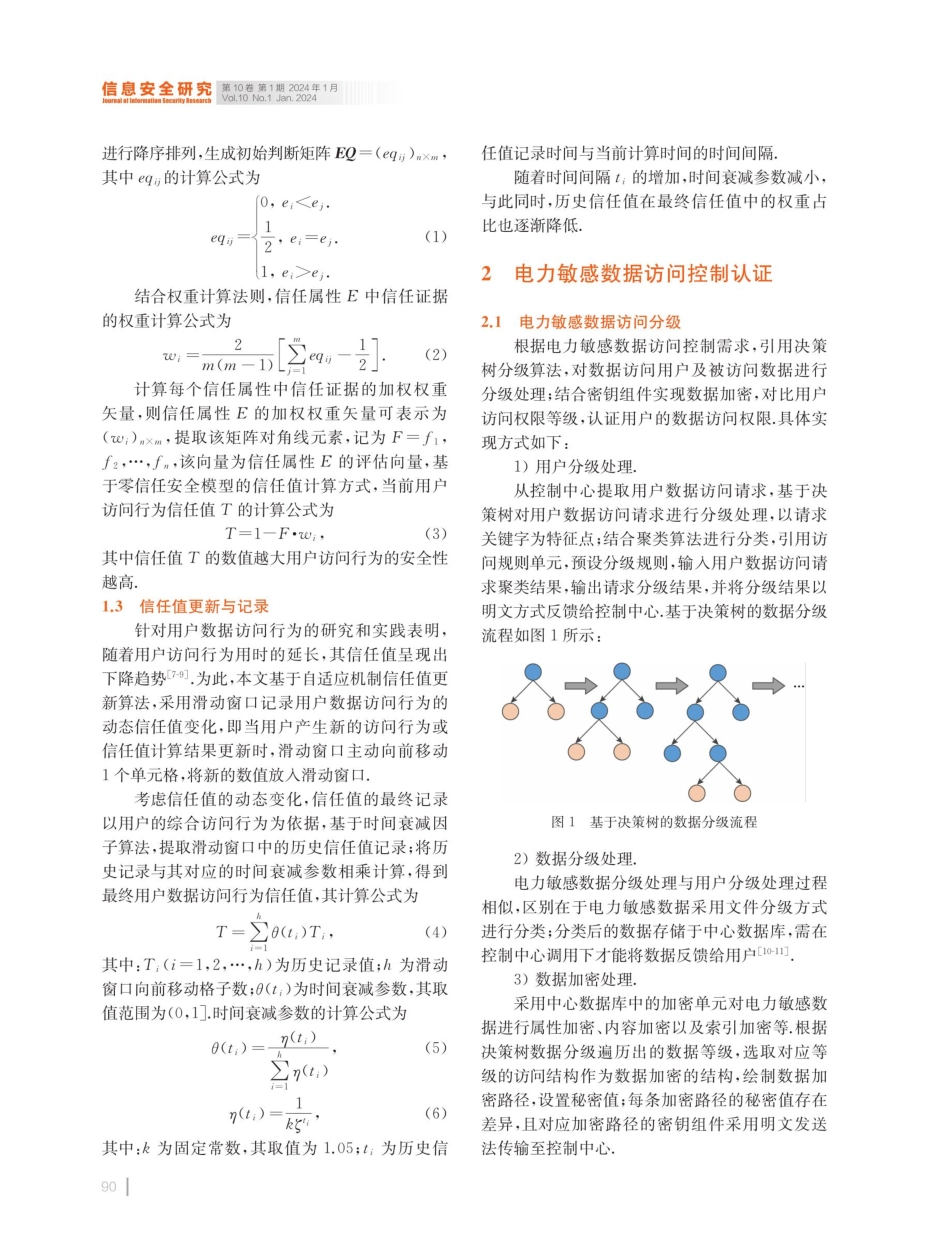
信息安全研究第10卷第1期2024年1月lournalotlinfermatienSecuriryBesearchVol.10No.1Jan.2024DOl:10.12379/j.issn.2096-1057.2024.01.14基于零信任安全模型的电力敏感数据访问控制方法林奕夫陈雪许媛媛”法汤晓冬”唐仁杰”边珊”1(国网福建省电力有限公司经济技术研究院福州350013)2(中国电力科学研究院有限公司北京100192)3(上海物盾信息科技有限公司上海201100)(yf.lin@qq.com)PowerSensitiveDataAccessControlMethodBasedonZeroTrustSecurityModelLinYifu',ChenXue',XuYuanyuan?,TangXiaodong",TangRenjie",andBianShan'1(EconomicandTechnologicalResearchInstituteofStateGridFujianElectricPowerCo.,Ltd.,Fuzhou350013)2(ChinaElectricPowerResearchInstitute,Beijing100192)3(ShanghaiWudunInformationTechnologyCo.,Ltd.,Shanghai201100)AbstractInordertoprotectthesecurityofpowersensitivedata,theaccesscontrolmethodofpowersensitivedatabasedonzero-trustsecuritymodelwasproposed,aimingattheproblemoflargeamountofleakageofpowersensitivedatacausedbythedifficultyofdataaccesscontrolandtheincreaseofdatatheftinbigdataenvironment.Basedonthezero-trustsecuritymodel,thispapercollectedthetrustfactorsofusers'accessbehavior,constructedthezero-trustsecuritymodel,decomposedthetrustattributesbyusingthehierarchicaldecompositionmodel,constructedajudgmentmatrixbasedontheweightdistributionmethodtocalculatethetrustvalueofusers'accessbehavior,andcombinedtheadaptivemechanismandthetimedecayalgorithmtoimprovetheupdateandrecordofthetrustvalue.Thehierarchicalgrowthdecisiontreeisusedtoclassifytheaccessofpowersensitivedata.Onthebasisofuserauthentication,signcryptionparametersareset,andpublicandprivatekeysareusedtosigntheaccessauthenticationinformation.Theexperimentalresultsshowedthatthismethodcaneffectivelysuppresstheviciousdataaccessbehavior,andthedataencryptiontimeoverheadwaslow,theaveragetimeoverheadwaslessthan1.4s/1200,andtheaccesscontrolerrorratewaslessthan5%.Theoverallcontroleffectreachedtheidealstandard.Keywordszerotrustsecurity;powersensitivedata;sensitivedataaccess;accesscontrol;weightallocationmethod摘要针对大数据环境下数据访问控制难...