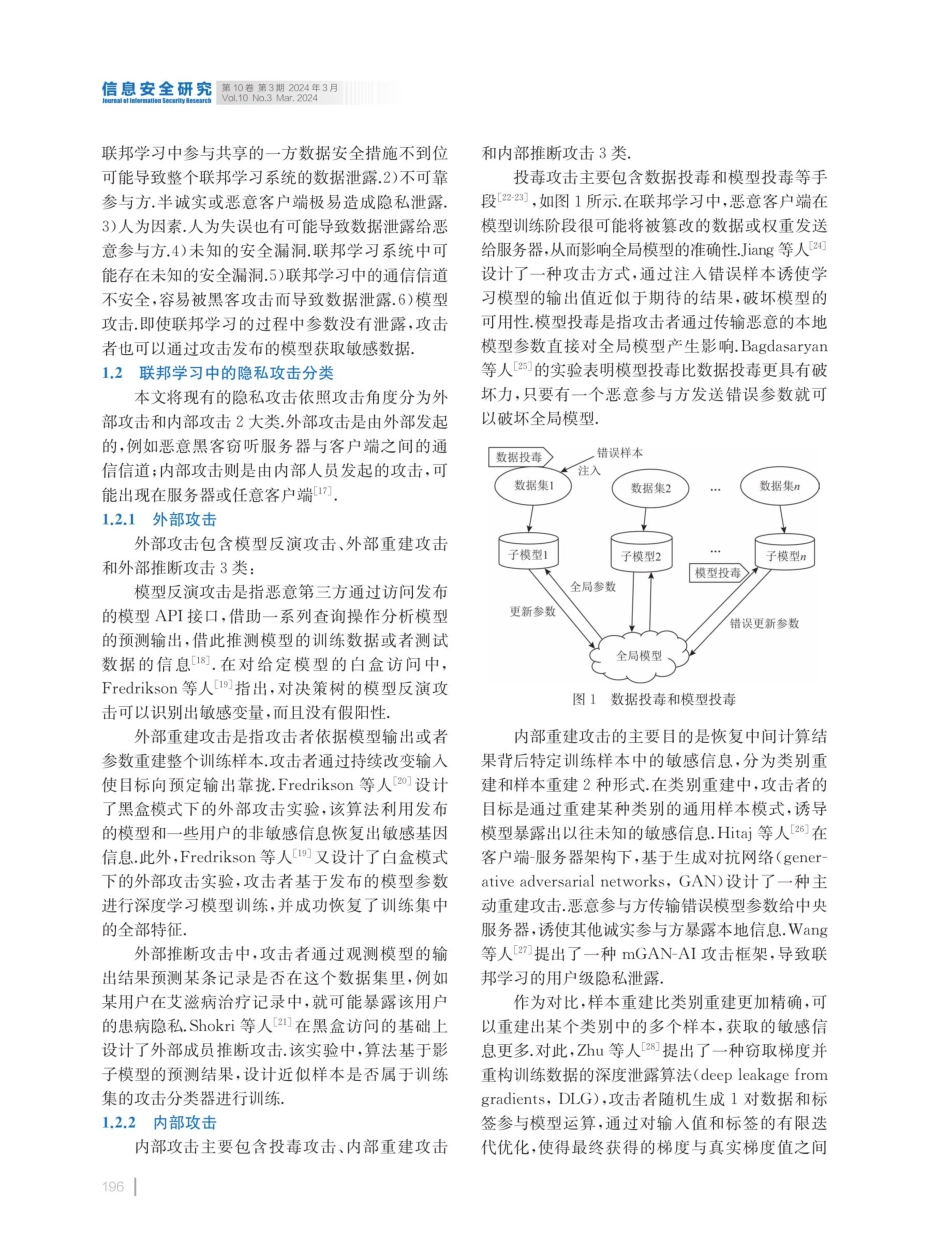
信息安全研究第10卷第3期2024年3月JournalotinformationSecurityResearchVol.10No.3Mar.2024DOl:10.12379/j.issn.2096-1057.2024.03.01联邦学习中的隐私保护技术研究刘晓迁许•飞马卓袁明1,钱汉伟1(江苏警官学院计算机信息与网络安全系2(南京邮电大学计算机学院完南京210023)3(南京大学软件学院南京210023)(lxqlara@163.com)ResearchonPrivacyProtectionTechnologyinFederatedLearningLiuXiaoqian',XuFeil,MaZhuo',YuanMingl-2,andQianHanweil.31(DepartmentofComputerInformationandCyberSecurity,JiangsuPoliceInstitute,Nanjing210031)2(SchoolofComputerScience,NanjingUniversityofPostsandTelecommunications,Nanjing210023)3(SoftwareInstitute,NanjingUniversity,Nanjing210023)AbstractInfederatedlearning,multiplemodelsaretrainedthroughparametercoordinationwithoutsharingrawdata.However,theextensiveparameterexchangeinthisprocessrendersthemodelvulnerabletothreatsnotonlyfromexternalusersbutalsofrominternalparticipants.Therefore,researchonprivacyprotectiontechniquesinfederatedlearningiscrucial.Thispaperintroducesthecurrentresearchstatusonprivacyprotectioninfederatedlearning.Itclassifiesthesecuritythreatsoffederatedlearningintoexternalattacksandinternalattacks.Basedonthisclassification,itsummarizesexternalattacktechniquessuchasmodelinversionattacks,externalreconstructionattacks,andexternalinferenceattacks,aswellasinternalattacktechniquessuchaspoisoningattacks,internalreconstructionattacks,andinternalinferenceattacks.Fromtheperspectiveofattackanddefensecorrespondence,thispapersummarizesdataperturbationtechniquessuchascentraldifferentialprivacy,localdifferentialprivacy,anddistributeddifferentialprivacy,aswellasprocessencryptiontechniquessuchashomomorphicencryption,secretsharing,andtrustedexecutionenvironment.Finally,thepaperanalyzesthedifficultiesoffederatedlearningprivacyprotectiontechnologyandidentifiesthekeydirectionsforitsimprovement.Keywordsfederatedlearning;privacyattack;differentialprivacy;homomorphicencryption;privacyprotection摘要联邦学习中多个模型在不共享原始数据的情况下通过参数协调进行训练.大量的参数交...